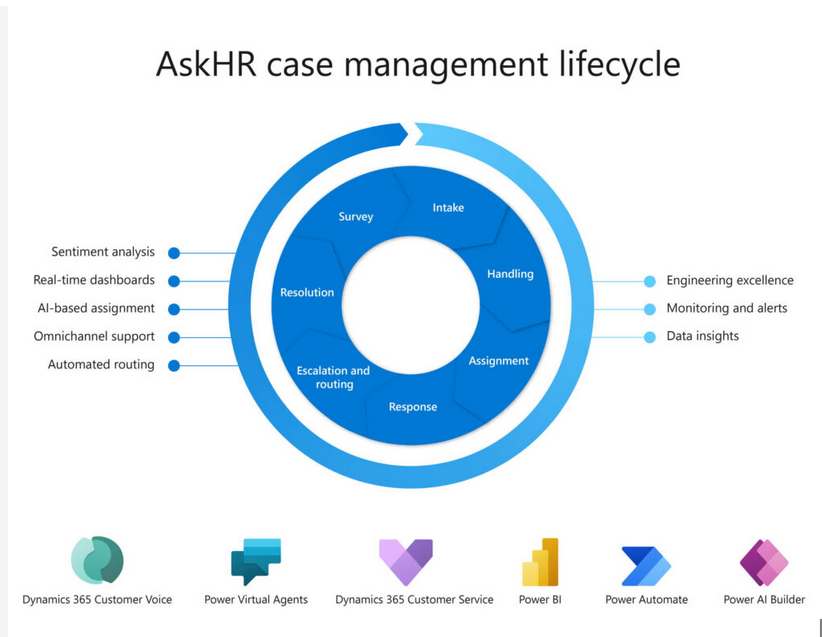
Data protection in other AWS services Data protection is a multi-faceted endeavor that encompasses a […]
SSM Parameter Store in the real world – Introduction to AWS Security Services
SSM Parameter Store in the real world To understand how SSM Parameter Store functions in […]
Who should use SSM Parameter Store or Secrets Manager? – Introduction to AWS Security Services
Who should use SSM Parameter Store or Secrets Manager? SSM Parameter Store is particularly well-suited […]
Best practices for secrets management – Introduction to AWS Security Services
Best practices for secrets management Whether you opt for SSM Parameter Store, Secrets Manager, or […]
Identifying and protecting sensitive data – Introduction to AWS Security Services
Identifying and protecting sensitive data As the risk of data exposure grows, it is essential […]
Macie in the real world – Introduction to AWS Security Services
Macie in the real world To illustrate Macie’s effectiveness, let’s delve into a scenario where […]
Unpacking threat and vulnerability detection – Introduction to AWS Security Services
Unpacking threat and vulnerability detection The cybersecurity landscape is an ever-evolving battlefield, rife with emerging […]
Detective in the real world – Introduction to AWS Security Services
Detective in the real world To understand the practical application of Detective, let’s consider its […]
Who should use Inspector? – Introduction to AWS Security Services
Who should use Inspector? Inspector is particularly useful for: CloudTrail Lake and Security Lake—your AWS […]
Who should use CloudTrail Lake or Security Lake? – Introduction to AWS Security Services
Who should use CloudTrail Lake or Security Lake? CloudTrail Lake is interesting for organizations that […]